Ensuring Security and Safety in using Remote Developer

1. Identity Verification in Remote Programming
Verifying the identity of remote programmers is the first line of defense against potential security threats. This section explores various methods, including document checks and background screenings, to establish the authenticity of individuals working remotely.
2. Secure Contract Signing
Contracts are the foundation of any professional relationship. Here, we delve into the critical aspects of creating secure contracts with remote programmers. Key clauses related to security, privacy, and intellectual property are discussed to mitigate risks effectively.
3. Utilizing Security Platforms and Tools
The choice of platforms and tools can significantly impact the security of remote programming projects. This section explores secure communication tools, version control systems, and collaboration platforms that contribute to a robust security infrastructure.

4. Open Source and Security Testing
Open-source code can enhance development speed but may introduce vulnerabilities. We discuss the importance of balancing open source with rigorous security testing. Regular assessments and testing methodologies are explored to identify and address potential security risks.
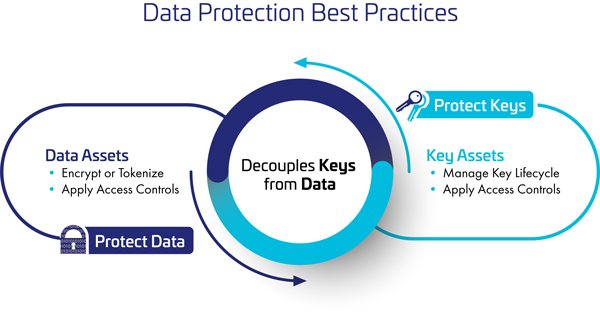
5. Data Encryption Best Practices
Protecting sensitive data is a top priority. This section covers the necessity of encrypting data during transmission and storage. Various encryption methods and tools are discussed to safeguard information against unauthorized access.
6. Establishing Comprehensive Security Policies
Building a strong foundation for security involves establishing comprehensive policies. We outline the key elements of security policies, covering data protection, access controls, incident response, and more.
7. Regular Assessments and Audits
Security is an ongoing process. This section emphasizes the importance of regular assessments and audits. Conducting thorough security audits ensures that the security measures in place are effective and that any vulnerabilities are promptly addressed.
In conclusion, securing remote programming environments requires a multifaceted approach. By implementing identity verification, secure contracts, utilizing the right tools, open source management, data encryption, robust security policies, and regular assessments, organizations can build a strong defense against potential security threats.
Hatonet connects onsite personnel IT companies in Vietnam, helping enterprises fully utilize the company’s human resources in an efficient and professional manner, and saving costs.
Connecting up to 400,000 people in the IT industry.
Save costs on finding headhunt partners.
Accompany and support in processes
Contact Us:
Email: hello@hatonet.com

.gif)